RealVu® Provides Unprecedented Fraud Protection
RealVu pre-bid validation code provides a clear path from buyer to seller, creating a holistic brand safe environment where fraud cannot flourish undetected.
RealVu Platform with Content Rendering Control (CRC ) validates every ad unit before delivery and follows the activity of the unit after the ad is delivered, measuring viewable impressions, monitoring URL authenticity in addition to dozens of other methods of verification.
RealVu’s unique architecture overcomes numerous vulnerabilities inherent in legacy server log file impression reporting methodology. Web server log impression counting allows for the creation of fraud in numerous ways and is easy to implement undetectably because the “impression” resides at the beginning of the communication chain in the ad delivery and reporting process (the server log record of the request).
In contrast, RealVu’s platform counts viewable impressions based on transmissions of data from viewer-side throughout the ad delivery process, directly to a server confirming the event, subsequent view time, and viewer’s interactions with the ad unit. With every ad selected for delivery, the RealVu dispatcher passes to the ad unit a unique token in an encrypted format. This token creates a closed communication channel as it passes with every message sent from or received by the ad unit during a reporting session of a viewable impressions. This assures that the tracking messages cannot be used to create fake messages such as Mutilated HTTP Packets Impression Fraud. RealVu collects every user agent that makes a request and keeps this data for analysis. RealVu employs a series of automated procedures for data analysis, monitored daily by a RealVu analyst for suspicious activity. In addition, RealVu provides methods for users to analyze potential traffic anomalies.
Iframes
Cross domain Iframes create a “fraud enabled” environment where bad players can engage in numerous methods of impression fraud.
RealVu prevents multiple types of impression fraud which is enabled by cross domain Iframes (e.g. intentional placement of RealVu tags on the document within an Iframe outside of the viewable area of the frame’s window or when the Iframe itself is positioned on the page outside of the viewable area or invisible because of its 0 x 0 px or 1 x 1 px size).
Iframe fraud appears in the RealVu system reports like this:
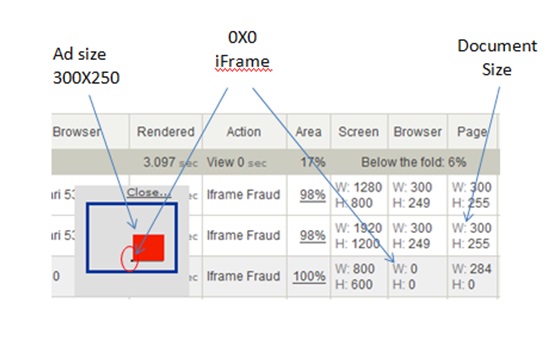
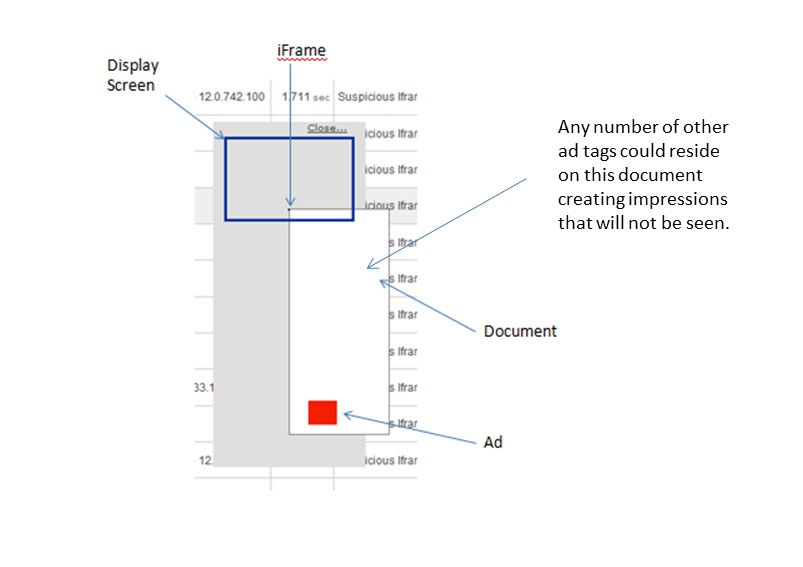
Iframes of a different domain which contain a larger sized document than the Iframe (fraud enabled) look like this in the RealVu report.
Layering Ads
Impression fraud may be committed by intentionally layering ads so the one on top is visible, but impressions are counted for all of the ads, including the ones underneath that are not visible. When RealVu tags are placed overlapping each other, the first will be pushed to the top and will load, render, and may report a viewable impression. All RealVu tags under the first are prohibited from rendering or reporting a viewable impression.
Invisible Re-Direct
If a RealVu tag is embedded on a web-page that is set to automatically re-direct to another web-page before the ad content can load and render within the visible area of the browser window for at least one second, a viewable impression will not be reported. This type of re-direct is typically invisible to the viewer and used to forge impressions by firing the ad tags on a page the viewer never sees.
Mutilated HTTP Packets Impression Fraud
Mutilated or Poisoned HTTP Packets Impression Fraud is an attack that can be qualified as a simplified version of a more general case, the Man-in-the-Middle (MITM) attack. It is a very effective way to create fraudulent impressions. Impressions created as a result of such an attack looks absolutely legitimate from a reporting stand point and cannot be verified as it is a one time HTTP request with no feedback in the process. The MITM attack is well described at: http://www.owasp.org/index.php/Man-in-the-middle_attack.
The MITM attack intercepts a communication between two systems. For example, in an HTTP transaction the target is the TCP connection between client and server. Using different techniques, the attacker splits the original TCP connection into two new connections, one between the client and the attacker and the other between the attacker and the server. Once the TCP connection is intercepted, the attacker acts as a proxy, being able to read, insert, and modify the data in the intercepted communication. MITM techniques, in cases when it is utilized for ad impression fraud, is more simple and doesn’t even have to break down the original connection between a user computer and a tracking server. The attacker only intercepts HTTP requests and stores them for a while. Due to the open text nature of HTTP protocol, the attacker is able to mutilate or “poison” the HTTP request header data to make a request look like it was sent from a different machine or browser. After a random time delay, the attacker sends the mutilated packet to the tracking server.
When “impression” measurement methodology is based on a simple log of requests sent from beacon images or Iframe SRC requests, there is no way to distinguish the “original impression” request and an attacker’s mutilated packet clones. That makes “impression” as a measurement metric not reliable in its nature.
The RealVu technology and the “viewable impression” methodology itself reliably protect accuracy of the metrics from being compromised by such attacks. The RealVu tracking architecture is based on encrypted feedback technology that creates a closed channel of communications between the ad and the tracking server. If an attacker modifies intercepted tracking messages or repeats its request it will not affect the measurement of viewable impression but expose the attacker.
